New Voldemort malware infects your machine by hiding itself as a fake PDF file: Here’s how it works
According to a report by Proofpoint, the Voldemort malware uses Google Sheets to issue new commands and store information stolen from infected devices.
 Voldemort malware is currently targeting organisations in the U.S, Europe and Asia. (AI Generated)
Voldemort malware is currently targeting organisations in the U.S, Europe and Asia. (AI Generated)A new malware campaign is reportedly wreaking havoc on thousands of Windows systems worldwide.The undocumented backdoor, named “Voldemort” is targeting organizations by impersonating tax agencies from North American, European and Asian countries.
According to a recent report by Proofpoint, the campaign started last month and has sent over 20,000 emails targeting over 70 organisations with half of these belonging to sectors like aerospace, insurance, education and transportation. At its peak, the campaign sent over 6,000 emails in a single day.
While the threat actor behind the campaign is still unknown, it looks like their main objective is to conduct cyber espionage.
How does Voldemort work?
According to Proofpoint, the attackers start by sending phishing emails to an organisation using its publicly available information. Depending on the geographical location, the email impersonates tax authorities from that country with links that will take them to the updated tax information.
When users click on the link, the recipients are then brought to a landing page hosted on “InfinityFree” which uses a Google AMP cache URL to redirect the victims to a new page with a “Click to view document” button.
If the victim is using Windows, the malware then asks users to download a hidden LNK file that disguises itself as a fake PDF with a shortcut arrow at the bottom left. For those wondering, LNK files are shortcuts to access files, folders and websites.
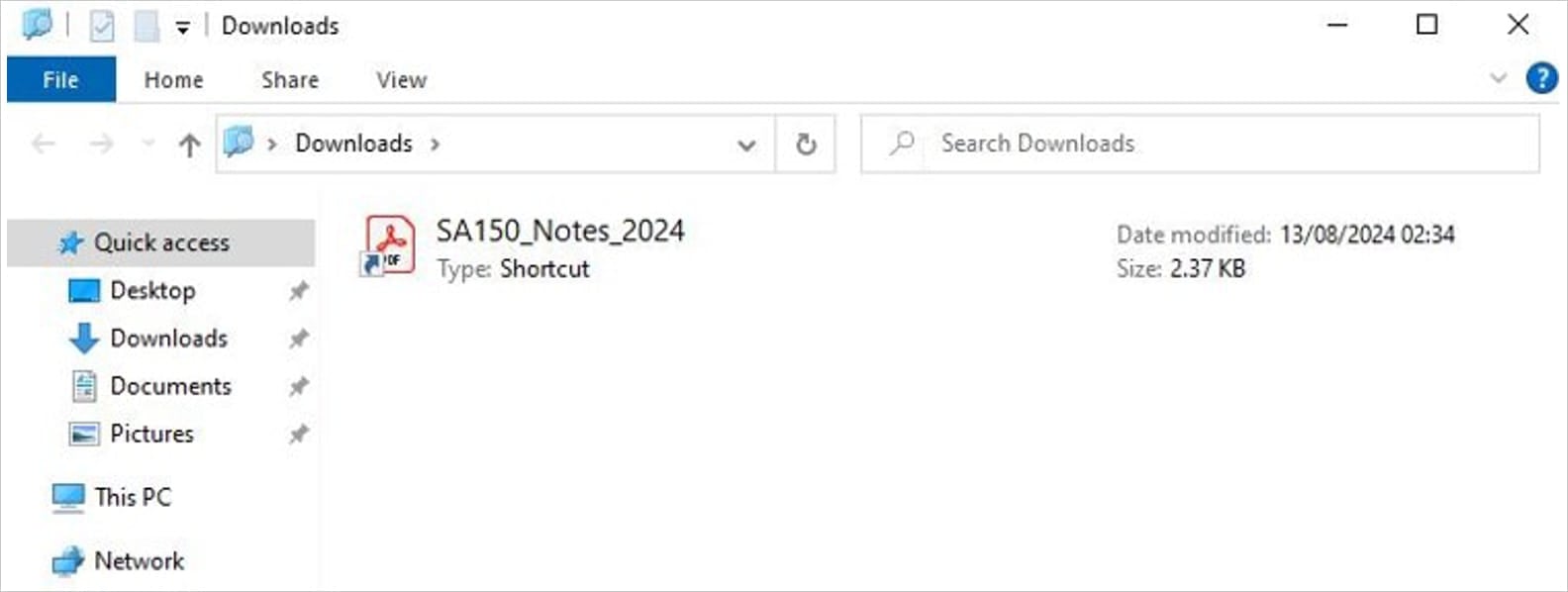 Here’s how the fake PDF looks like. (Image Source: Proofpoint)
Here’s how the fake PDF looks like. (Image Source: Proofpoint)
Opening the fake PDF executes a Python script that hides its background activity by showing a PDF document, following which the script downloads a malicious DLL to load Voldemort into the memory.
Once Voldemort infects the machine, it uses Google Sheets as a command and control server to get new commands and store your stolen data. The malware even uses Google API to interact with Google Sheets via an encrypted channel, which makes it even harder to detect or get flagged by security tools.
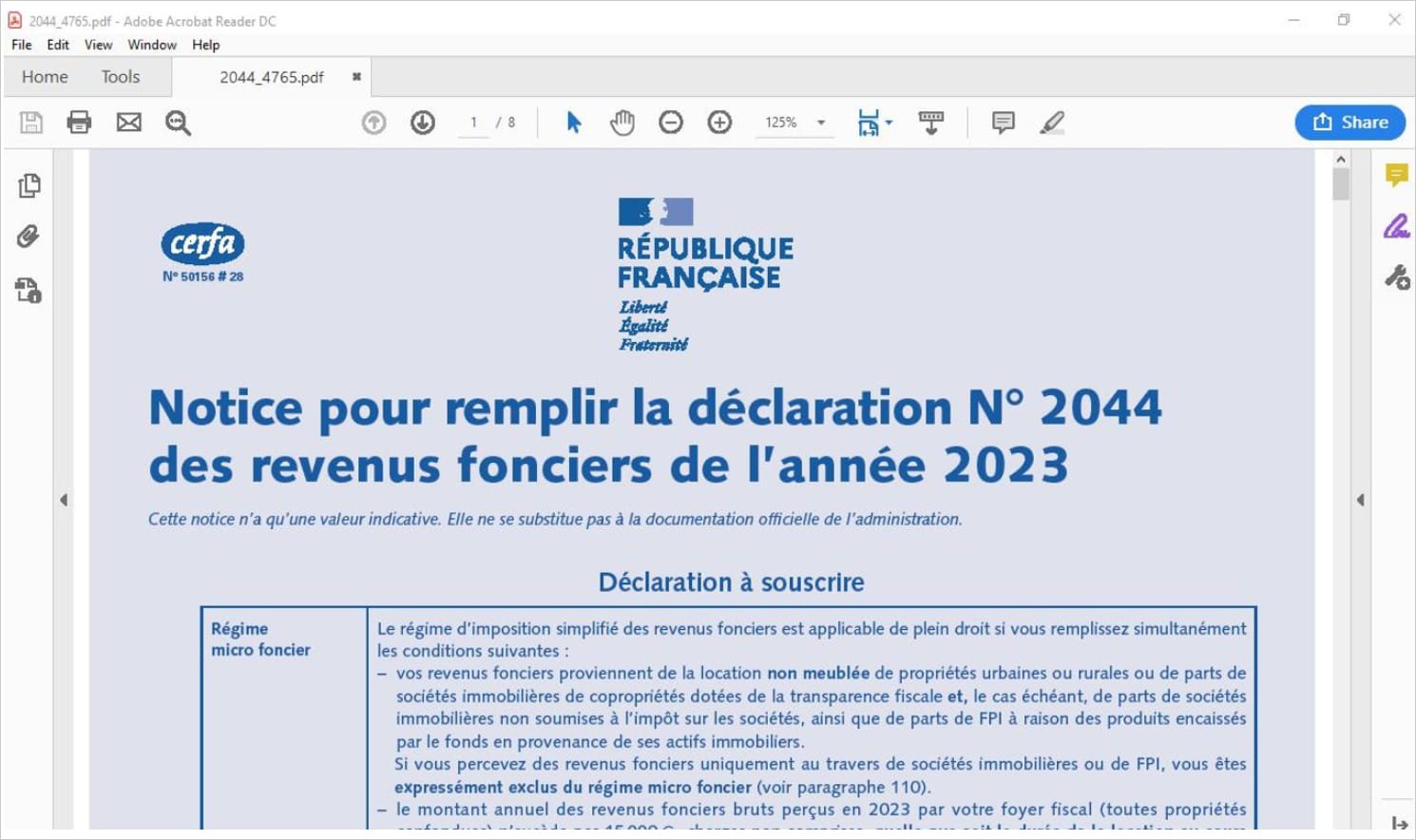 It even shows a decoy PDF to the user. (Image Source: Proofpoint)
It even shows a decoy PDF to the user. (Image Source: Proofpoint)
How do I protect myself against Voldemort?
Since this is fileless malware, your antivirus may not be able to catch anything, so if you happen to open the file by accident, your best bet is to do a clean Windows installation. Alternatively, Proofpoint recommends that you should limit access to external file sharing services, block connections to TryCloudflare if you don’t need it or monitor PowerShell for suspicious activities.
However, since the threat actors behind Voldemort are currently targeting organisations, it is highly unlikely that you will get the phishing email on your personal account. But for those with a workplace email address should refrain from downloading documents or files from unknown senders or those outside their organisation.







